In July 2020 the Court of Justice of the European Union’s (CJEU) Schrems II decision declared the EU-US Privacy Shield Protections inadequate for the protection of European data. On November 10, 2020, the European Data Protection Board (EDPB) released “Recommendations 01/2020 on measures that supplement transfer tools to ensure compliance with the EU level of protection of personal data.” The recommendations provide a framework for data exporters to analyze the protections afforded to European Union residents’ person data and ensure that throughout the data lifecycle data receive the protection demanded by EU privacy law as embodied in the GDPR and other regulations.
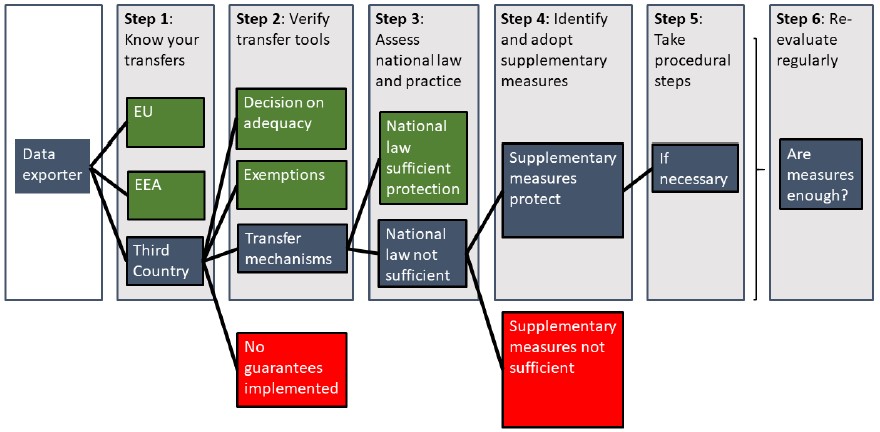
The recommendations provide six steps to analyze the processing of personal data to ensure compliance with the GDPR following Schrems II.
- Know your transfers. Map all transfers of personal data and be aware of the countries data pass through. Data transfers must also be adequate, relevant and limited to what is necessary to the purposes for which it is transferred to and processed in the third country. Note that remote access from a third country also counts as a transfer.
- Verify your transfer tools. The European Commission has already declared some country, region or sectors for data transfer as adequate. In the absence of an adequacy decision, rely on one of the transfer tools listed under Article 46 GDPR for transfers that are regular and repetitive. In some cases of occasional and non-repetitive transfers you may be able to rely on one of the derogations provided for in Article 49 GDPR.
- Assess the law or practice of the third country. For evaluating the elements to consider when assessing the law of a third country the EDPB provided a document of “European Essential Guarantees recommendations.” These recommendations suggest considering issues such as the legislation governing data access by public authorities.
- Identify and adopt supplementary measures. Depending on the country assessment, supplementary measures may be necessary to bring the level of protection of the data transferred up to the EU standard of essential equivalence. Annex 2 includes a non-exhaustive list of supplementary measures with some of the conditions they would require to be effective. In some cases no supplementary measure can ensure the necessary data protection and such transfers must be avoided.
- Take any formal procedural steps your supplementary measures may require.
- Re-evaluate at appropriate intervals the level of protection afforded data you transfer to third countries and monitor if there have been or will be any developments that may affect it.
Definitions
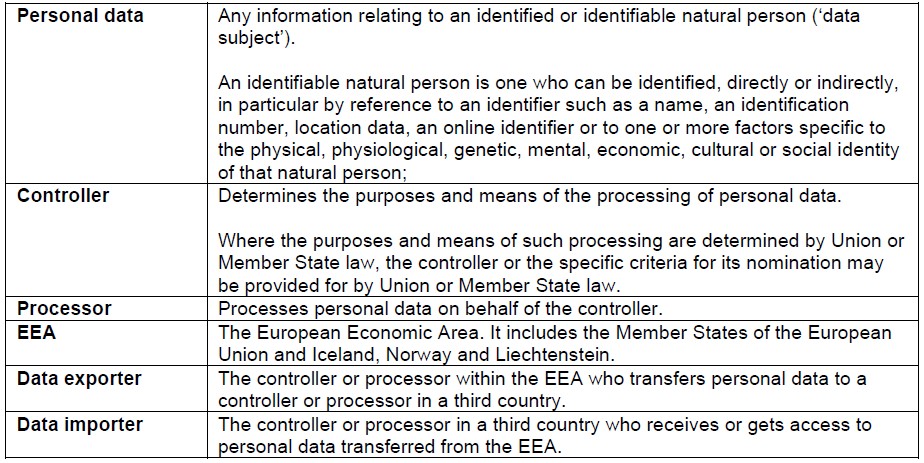
European data protection uses the following definitions, some of which are included in the recommendations.
Transfer Tools
Transfer tools include such measures as:
- standard data protection clauses (SCCs);
- binding corporate rules (BCRs);
- codes of conduct;
- certification mechanisms; and
- ad hoc contractual clauses.
Assessing law and practice
Transfer tools must be evaluated in light of the national law and practice to determine if the selected transfer tool effectively protects privacy. The EDPB European Essential Guarantees (EEG) recommendations provide the framework to evaluate national policies. Such evaluation is best done by privacy experts in ways that can be reused for many clients’ needs. The CJEU held that US national law was not sufficient to protect European residents’ personal data in Schrems II. The lack of bright line rules in evaluating country law and policy means there may be arguments that no countries meet the national privacy requirements. Law and practice assessments are ongoing.
Supplementary measures
Supplementary measures are primarily technical procedures to limit disclosure of data to unauthorized persons. The non-exhaustive list in Annex 2 of the recommendations includes such examples as:
- encrypting data stored in a suspect country where the decryption keys are not accessible in the suspect country;
- pseudonymised data;
- split or multi-party processing that prevents any individual holder of partial data from reconstituting the data for unauthorized purposes.
Conclusion
The recommendations have been eagerly anticipated. While they provide a helpful framework to carefully evaluate privacy issues, they do not provide any objective criteria for evaluating self-compliance. As has always been the case, the most significant step is to know and understand the data collected, how it is handled, and how it is transferred during the data life cycle.
